SSH Attacks
When you run a UNIX based system on the internet you will see many login attempts. You will quickly find out these aren't mistakes but real attacks when you accidently connect a test system with a weak root password. Attackers are constantly trying to guess the passwords of various accounts on your systems in order to gain access
This type of attack is pretty simple, but still some questions arise. Which tools are used? How do the attackers proceed and where do they come from? And most interestingly: What will they do with my system when they get access?
The use of honeypots
Bears can be attracted using honey. Hackers can be studied using so called honeypots which pretend to be vulnerable to specific attacks. To find out more about the attackers and what they actually do, Torsten Voss and Andreas Bunten used several types of honeypots to study them.
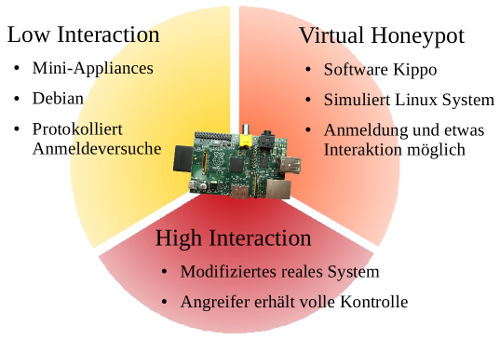
Different types of honeypots let us extract different kind of information:
- Low Interaction Honeypots:
These types of systems accept SSH connections and log all parameters connected with the login attempt without ever giving out an interactive session. This way an overview can be gained of the accounts attacked as well as the passwords and tools used. ARM based systems on a chip (SoC) are used together with Debian Linux.
- Virtual Honeypots:
A vulnerable linux system is simulated. Login by SSH seems to be possible if the weak password is guessed. In reality, the attacker is connected to the honeypot software which simulates a normal linux shell. The possibility to interact with the honeypot allows us to collect more information about what the attackers do and what tools are used after the initial attack.
- High Interaction Honeypots: Here, the attackers are given full control over a system. There are security mechanisms to prevent outgoing attacks which are very difficult to spot. High interaction honeypots allow a much closer study of what attackers are doing. Using this kind of honeypot also requires the most effort since manual monitoring is used to disconnect the honeypot from the network if something goes wrong.
During our investigation, we quickly realised that most attacks originate on compromised systems. These results were first published on the LinuxTag 2012 in Berlin [1]. Further information can be found in an UpTimes article [2]. In most cases, the attacking systems run an SSH server themselves and can be recognised by their hostkey even when IP addresses are changed. We compared different ways to recognise attacking systems and found SSH hostkeys to be more stable than using the source IP. The statistical data was presented on the proceedings of the 20. DFN Workshop in Hamburg [4]. Further information has been presented at the Frühjahrsfachgespräche 2013 of the German UNIX User Group (GUUG) in Frankfurt [5]. A closer look at the SSH hostkeys revealed more mysteries; e.g. a few keys are present on hundreds of systems seemingly unrelated to another (Secure Linux Administration Conference (SLAC) 2013 in Berlin [8], Uptimes 3/2013 [9]).
Recording of the talk Dr Bruteforce - Oder wie ich lernte SSH-Angriffe zu lieben at SLAC 2013 in Berlin [8]
Honeypots can be used for more than investigating SSH attacks. In an article in the information security magazine KES various ways of using honeypots in commercial environment were presented [6]. Building on the SSH honeypot data, Denise Muth created an abstract modell for server compromises (20. DFN Workshop in Hamburg [5]).
We got a lot of support by hosting ARM based Low Interaction Honeypot Systems. We would like to thank Guido, Barbara, Sabine, Agnes, Josef, Eve und Christel for their help!
[1] Andreas Bunten und Torsten Voss: Wie man SSH-Angreifern mit Linux Honeypots nachstellt, Vortrag auf dem 18. Linux Tag in Berlin, Mai 2012 (local copy)
[2] Andreas Bunten und Torsten Voss: Stille Beobachter, Uptimes - Mitgliederzeitschrift der German Unix User Group, Ausgabe 2 - 2012, S. 13ff (local copy)
[3] Homepage des DenyH0st Projekt: http://denyhosts.sourceforge.net
[4] Andreas Bunten und Torsten Voss: SSH-Honeypots und neue Schutzmaßnahmen gegen Brute Force Angriffe, im Konferenzband des 20. DFN Workshops, Februar 2013 (local copy)
[5] Denise Muth: Generischer Ablauf von Serversystemeinbrüchen - Analyse und Konzeption, 20. DFN Workshops, Februar 2013
[6] Andreas Bunten und Torsten Voss: Die Admins schlagen zurück: SSH-Angreifern mit Honeypots über die Schulter schauen, GUUG Frühjahrsfachgespräch, Februar 2013 (local copy)
[7] Andreas Bunten: Honeypots im Unternehmen, <kes> – Die Fachzeitschrift für Informations-Sicherheit, Ausgabe 2 - 2013, S. 66ff
[8] Andreas Bunten und Torsten Voss: Dr Bruteforce - Oder wie ich lernte SSH-Angriffe zu lieben, 6. Secure Linux Administration Conference (SLAC), Berlin Juni 2013 (local copy)
[9] Andreas Bunten und Torsten Voss: Winterkrimi 2013: Die rätselhaften SSH-Hostkeys, Uptimes - Mitgliederzeitschrift der German Unix User Group, Ausgabe 3 - 2013, S. 9ff (local copy)