Honeypots
The data generated with the help of low interaction honeypots allow to gain a broad overview regarding attack activity. The user accounts targeted, the passwords tried and connections parameters are logged. For the following graphs 602698 login attempts grouped in 1909 attackes during spring 2012 have been evaluated.
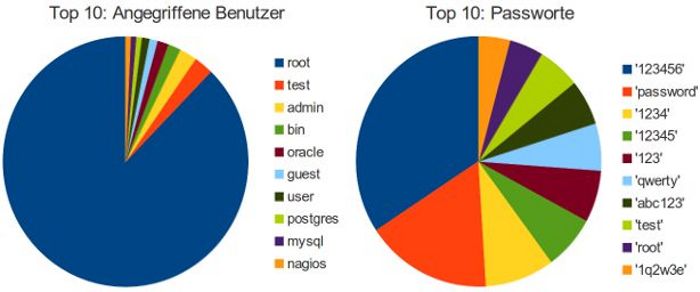
Attackers mostly aim for the account 'root'. It's always there and also has the most access rights. All in all, a third of all login attempts were made for the account 'root'. Looking closer at all the other login attempts (e.g. all accounts besides 'root'), we found 225366 attempts with username equals password. So in the end, the most common password is not '123456' but the name of the targeted user. Besides those obvious guesses, we detected some strange login attempts with passwords like !!!geogenak123$$$ or !#EWDYUWU*(&@#YEDS. Some surprising usernames targeted were Terminator, username, or thisisalongusername. Also, the length of the attack varied a lot:
- There were 315 login attempts per attack on average.
- The median was only 31 trials per attack.
- The most common found attack size is even lower: 15 login trials.
- The high average is caused by few very large attacks. The largest consisting of 30689 login trials.
Virtual Honeypots
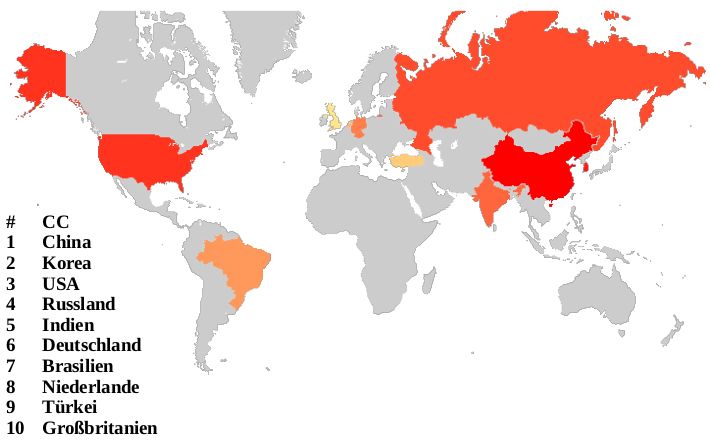
The attacks can be analysed by the origin of the IP address of the attacking system. Using whois one can easily assign a country to each source ip. When we count where the most attacks seem to come from China takes the lead followed by Korea and the United States of America:
The attackers can actually log on to the virtual honeypots and it is possible to distinguish between automated attack tools and the real attackers. When you look at the countries the humans behind the attacks log on from a completely different map appears. Here, Romania leads the way followed by the United States of America and Italy:
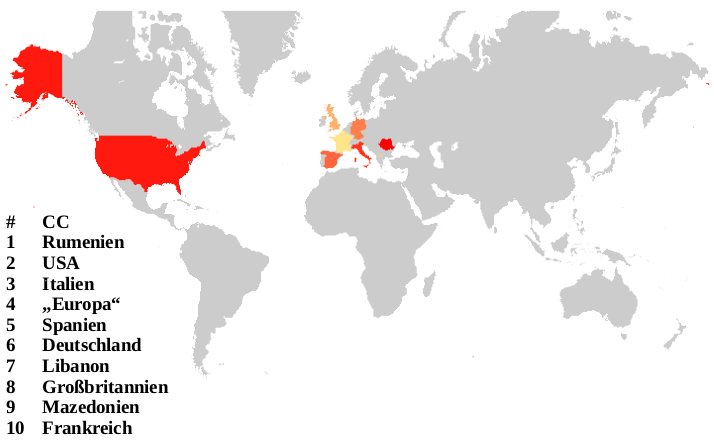
Since the virtual honeypots only simulate a vulnerable system, most attackers realise after a while they are being fooled.
High Interaction Honeypots
High Interaction Honeypots take the game a step further. Here, it will be difficult for the attackers to spot the problem. In this video a session of an attacker connected to a high interaction honeypot can be seen. The IP address of the attacker and the URLs used to download malware have been masked: